We understand for any business, one size does not fit all
At Approved Systems, we understand that one size does not fit all. Our flexible packages are designed to suit your unique business requirements, offering both fixed monthly rates and hourly support packages.
Comprehensive Managed IT Services
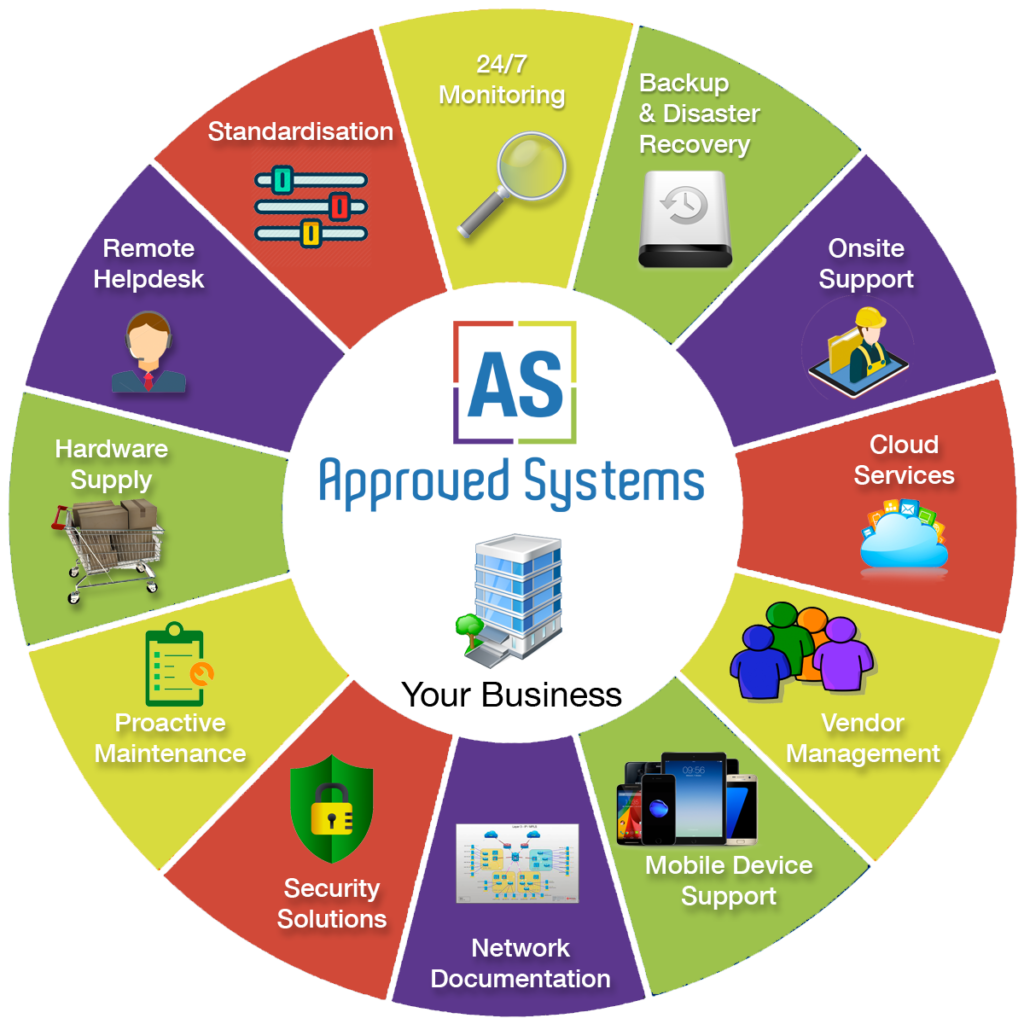
Managed Services Examples
These are just examples of combined services Approved Systems can put together to make a complete Managed Services Solution (MSS)
Retail Shopfront
Example of services available (but not limited to)
- Point of Sale PC Maintenance
- PC Backups
- Internet / Router / Firewall
- Redundant 4G Backup Internet
- Staff Wifi and Optional Public Wifi
- Site to Site Virtual Private Networks
- A.I. Intelligent Surveillance Systems
- IP Desk Phones and Cordless Phones
- Electrical Test and Tag
- Virtual Fax Line (Fax to Email)
Small Office / Home Office (SOHO)
Example of services available (but not limited to)
- Internet/Router/Wi-Fi Management
- Redundant 4G Backup Internet
- Computer Maintenance
- Site-to-Site VPNs
- Remote Access Back to the Office
- PC Backups
- Mobile Phone SIM Plans
- IP Desk and Cordless Phones
- Electrical Test and Tag
- Virtual Fax Line (Email2Fax and Fax2Email)
Medium Business
Example of services available (but not limited to)
- Internet/Wi-Fi/Router/Firewall Management
- Redundant 4G/5G Backup Internet
- Microsoft 365 Account and License Management
- Active Directory and Exchange Online Mail
- Intune Endpoint Policies
- Governance and Compliance Policies
- SharePoint/Teams/OneDrive Management
- PC Maintenance and Backups
- Working from Home VPN
- Network Attached Storage
- IP Desk and Cordless Phones
- Electrical Test and Tag
- Virtual Fax Line (Email2Fax and Fax2Email)
Enterprises / Large Companies
Example of services available (but not limited to)
- High-Speed Internet Access
- Redundant Internet Solutions
- Microsoft 365 Account and License Management
- Azure Active Directory Syncing with On-Prem AD
- Active Directory and Exchange Online Mail
- Intune Endpoint Policies
- Governance and Compliance Policies
- SharePoint/Teams/OneDrive Management
- PC Maintenance and Backups
- Working from Home VPN
- On-Premises Server and Storage Support and Backups
- IP Desk and Cordless Phones
- Electrical Test and Tag
- Virtual Fax Line (Email2Fax and Fax2Email)
ESSENTIAL EIGHT RISK MITIGATION STRATEGIES
The Essential Eight is a baseline risk mitigation strategy recommended by the Australian Department of Defence’s intelligence agency known as the Australian Signals Directorate (ASD). Implemented successfully, Essential Eight can mitigate cyber security risks for your organisation.
Essential Eight mitigates common cyber security risks and limits the extent of incidents when they happen. It takes you through these baseline risk mitigation strategies which Professional Advantage can help you put in place:
- Application Whitelisting
Allow only trusted and approved applications to run on your network. This prevents execution of malicious programs from automatically running by having a set of pre-approved apps. - Application Patching
Determine patching procedures and levels for popular web browsers, Microsoft Office, Oracle Java and PDF viewers. This would help mitigate vulnerabilities on apps that need patching. - Operating System Patching
Determine existing patching systems, patching schedules and server/workstation patching compliance. This should allow you to mitigate vulnerabilities on operating systems that need patching. - Restrictions of Administrative Privileges
Review admin privileges on specific IT systems and provide necessary permissions only for those who need them. - Configuration of Office Macros
Review office macros and current policies to prevent untrusted macros with malware from automatically running. - User Application Hardening
Ensure that unauthorised applications will not be utilised such as Adobe Flash Player or Java applets in browsers that have been known to deliver malware. - Multi-factor Authentication
Use a second factor such as a physical token or mobile device to make it more difficult for cyber criminals to access your systems even when the password has been breached. - Review Backups
Ensure regular backups of data so you can get it back in case you suffer a cyber-attack. Determine RTO/RPO, retention period, online/offline backups, offsite storage location and test restoration schedule.
Implementation of the Essential Eight will vary across organisations depending on potential adversaries and risk profile. It is important to undertake a comprehensive risk analysis prior to implementation to develop a sustainable security strategy.
Ultimately, establishing a security culture throughout an organisation is fundamental to risk mitigation. Well-developed and robust security strategies can be quickly and easily undone through human interaction.
Would you like us to assist in getting you above this baseline?
Windows Patch Management
Approved systems can provide a Windows Patch and Software upgrade scheduling service to ensure your fleet of computers are up to date and secure.
Data Protection
Approved Systems can manage your Workstation/Laptop backups to ensure you never lose important information, we offer:
- Onsite and offsite backups
- Disaster recovery & business continuity
- Quick restores
- File or image based backups
- Windows Backups (all server/workstation editions)
- Linux Backups
- Office365 Email, Teams, Sharepoint and OneDrive Daily Backups
- Daily monitoring including email notification
24/7 Helpdesk
The Approved Systems helpdesk is available either 9-5 or 24/7 to ensure you have the support you need when and where you need it the most. You’re also supported by a dedicated primary technician and account manager who understand and monitor your business IT environment, keeping across any issues you may have and helping you plan for your future IT needs.
